In a significant revelation shaking the cybersecurity landscape, researchers have unveiled DKnife, a highly sophisticated gateway-monitoring and adversary-in-the-middle (AitM) framework. Operated by a China-nexus threat actor since at least 2019, DKnife represents a formidable tool designed to compromise routers and edge devices, enabling deep packet inspection, traffic manipulation, and the insidious delivery of malware.
DKnife: A Linux-Based Modular Menace
At its core, DKnife is a collection of seven Linux-based implants, meticulously engineered to infiltrate network gateways. This modular architecture allows its operators to execute a wide array of malicious activities, from covert surveillance to active in-line attacks that replace legitimate downloads with harmful payloads. Cisco Talos researchers, who brought DKnife to light, emphasize its broad targeting capabilities, encompassing PCs, mobile devices, and even Internet of Things (IoT) devices.
Primary Targets and Operational Links
Initial assessments suggest a strong focus on Chinese-speaking users, evidenced by phishing pages tailored for Chinese email services, exfiltration modules for popular Chinese mobile applications like WeChat, and references to Chinese media domains within its code. However, the potential for broader regional targeting remains, especially given DKnife’s infrastructural ties to other prominent Chinese threat groups.
Cisco’s discovery of DKnife emerged from their ongoing monitoring of “Earth Minotaur,” another Chinese threat cluster known for tools like the MOONSHINE exploit kit and the DarkNimbus (also known as DarkNights) backdoor. Intriguingly, DarkNimbus has also been leveraged by “TheWizards,” a third China-aligned Advanced Persistent Threat (APT) group. Further analysis revealed an IP address within DKnife’s infrastructure hosting WizardNet, a Windows implant deployed by TheWizards via their own AitM framework, “Spellbinder.” This intricate web of connections underscores the collaborative and evolving nature of these state-sponsored cyber operations.
How DKnife Orchestrates Its Attacks
DKnife’s power lies in its ability to intercept and manipulate network traffic at critical junctures. Its components work in concert to achieve various objectives:
- dknife.bin: The Central Command
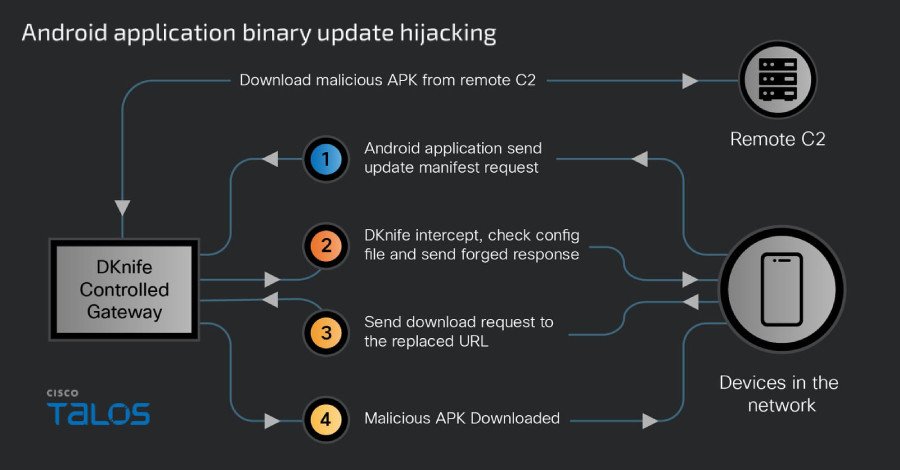
This core implant is the brain of the operation, responsible for deep packet inspection, reporting user activities, and executing binary and DNS hijacking. - postapi.bin: Data Exfiltration Relay
Acts as a relay, receiving intercepted traffic from other DKnife components and securely transmitting it to remote command-and-control (C2) servers. - sslmm.bin: TLS Termination & Credential Harvesting
A modified HAProxy module, it performs TLS termination, decrypts email traffic (POP3/IMAP), and reroutes URLs. Crucially, it inspects plaintext streams to extract usernames and passwords from major Chinese email providers. - mmdown.bin: Malware Updater
Connects to a hard-coded C2 server to download Android Package Kits (APKs) used for subsequent attacks. - yitiji.bin: Packet Forwarder
Creates a bridged TAP interface on the compromised router, enabling the hosting and routing of attacker-injected LAN traffic. - remote.bin: P2P VPN Client
Establishes a peer-to-peer VPN communication channel back to the remote C2, ensuring persistent access.
- dkupdate.bin: Watchdog & Updater
Ensures the continuous operation and updates of the various DKnife components, maintaining the framework’s resilience.
Deep Dive: DKnife’s Malicious Capabilities
The “dknife.bin” component, through its deep packet inspection capabilities, facilitates a range of nefarious activities:
- Malware Delivery: Serves updated C2 configurations to Android and Windows variants of the DarkNimbus malware. It also hijacks Windows and other binary downloads, using DLL side-loading to deliver the ShadowPad backdoor, which then loads DarkNimbus.
- DNS Hijacking: Conducts Domain Name System (DNS)-based hijacking over both IPv4 and IPv6, enabling malicious redirects for domains like JD.com.
- Application Update Hijacking: Intercepts update manifest requests for popular Android applications, including Chinese news media, video streaming, image editing, e-commerce, taxi services, gaming, and pornography apps, replacing legitimate updates with malicious versions.
- Anti-Antivirus Measures: Actively interferes with communications from antivirus and PC-management products, such as 360 Total Security and Tencent services, to evade detection.
- Real-time Monitoring: Continuously monitors user activity and reports it back to the C2 server, providing operators with a comprehensive view of compromised networks.
The Enduring Threat to Edge Devices
As Cisco Talos aptly notes, “Routers and edge devices remain prime targets in sophisticated targeted attacks.” The DKnife framework serves as a stark reminder of the critical importance of securing these often-overlooked network perimeters. Its modularity, sophisticated AitM techniques, and deep integration with other China-linked APT operations highlight an evolving and persistent threat that demands heightened vigilance from cybersecurity professionals and users alike.
For more details, visit our website.
Source: Link







Leave a comment