A New Era of Cyber Warfare: The AISURU/Kimwolf Botnet’s Unprecedented Attack
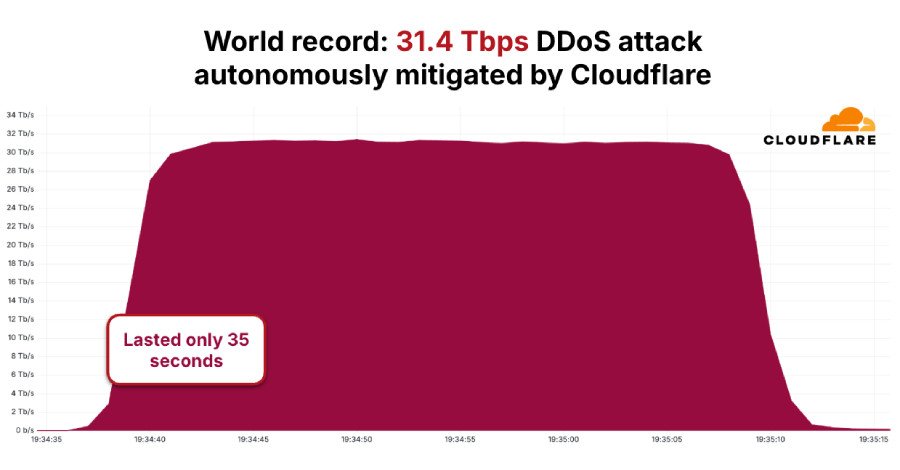
In a stark reminder of the escalating cyber threat landscape, the AISURU/Kimwolf distributed denial-of-service (DDoS) botnet has unleashed a record-setting attack, peaking at an astonishing 31.4 Terabits per second (Tbps). This hyper-volumetric assault, though lasting a mere 35 seconds in November 2025, signals a dangerous evolution in cyber aggression, as reported by Cloudflare, which successfully detected and mitigated the activity.
The Record-Breaking Deluge
The 31.4 Tbps attack stands as a testament to the sheer power and sophistication of modern botnets. This incident was not isolated; it was part of a broader surge in hyper-volumetric HTTP DDoS attacks orchestrated by AISURU/Kimwolf throughout the fourth quarter of 2025. Another significant campaign, dubbed ‘The Night Before Christmas,’ commenced on December 19, 2025. During this period, Cloudflare observed average attack sizes reaching 3 billion packets per second (Bpps), 4 Tbps, and 54 million requests per second (Mrps), with peak rates soaring to 9 Bpps, 24 Tbps, and 205 Mrps.
The Escalating DDoS Threat Landscape
The numbers paint a grim picture of the year 2025. Cloudflare’s Omer Yoachimik and Jorge Pacheco revealed a staggering 121% surge in DDoS attacks, with an average of 5,376 attacks mitigated every hour. The total number of DDoS attacks more than doubled from 2024, reaching an incredible 47.1 million. Network-layer DDoS attacks alone accounted for 34.4 million mitigations in 2025, a significant jump from 11.4 million in 2024. The fourth quarter of 2025 saw network-layer attacks comprising 78% of all DDoS activity, marking a 31% increase over the previous quarter and a 58% rise compared to 2024. Hyper-volumetric attacks in Q4 2025 surged by 40% quarter-over-quarter, from 1,304 to 1,824, with the size of these attacks growing by over 700% compared to late 2024.
Unmasking the Botnet: AISURU/Kimwolf and IPIDEA
The AISURU/Kimwolf botnet’s formidable strength is derived from a vast network of over 2 million compromised Android devices, predominantly off-brand Android TVs. These devices are often ensnared by tunneling through residential proxy networks like IPIDEA. IPIDEA, a Beijing-based company, is believed to have enrolled devices using at least 600 trojanized Android apps embedding various proxy SDKs, and over 3,000 trojanized Windows binaries disguised as legitimate software like OneDriveSync or Windows updates. Furthermore, IPIDEA has been found to advertise VPN and proxy apps that covertly transform users’ Android devices into proxy exit nodes without their knowledge or consent. The operators also run a dozen residential proxy businesses, all secretly connected to IPIDEA’s centralized infrastructure.
A Coordinated Defense: Google and Cloudflare Strike Back
In a significant counter-offensive, Google recently disrupted IPIDEA’s proxy network, initiating legal action to dismantle dozens of domains used for device control and traffic proxying. Collaborating with Cloudflare, Google also targeted IPIDEA’s domain resolution, severely impacting their ability to command and control infected devices and market their illicit services. This coordinated effort highlights the critical importance of industry collaboration in combating sophisticated cyber threats.
Q4 2025: A Snapshot of Global Cyber Vulnerabilities
Cloudflare’s observations for Q4 2025 also shed light on global attack patterns:
- Most Attacked Sectors:
Telecommunications, service providers, and carriers bore the brunt of attacks, followed by information technology, gambling, gaming, and computer software.
- Most Attacked Countries: China, Hong Kong, Germany, Brazil, the U.S., the U.K., Vietnam, Azerbaijan, India, and Singapore were the primary targets.
- Largest Sources of Attacks: Bangladesh surpassed Indonesia as the leading source of DDoS attacks, with Ecuador, Indonesia, Argentina, Hong Kong, Ukraine, Vietnam, Taiwan, Singapore, and Peru also featuring prominently.
Rethinking Cyber Defenses in a Volatile World
Cloudflare emphasizes that DDoS attacks are rapidly increasing in both sophistication and scale, surpassing previous expectations. This dynamic threat landscape poses a significant challenge for organizations to maintain adequate defenses. Companies still relying on on-premise mitigation appliances or on-demand scrubbing centers are strongly advised to re-evaluate and fortify their defense strategies to cope with these evolving, hyper-volumetric threats.
For more details, visit our website.
Source: Link







Leave a comment