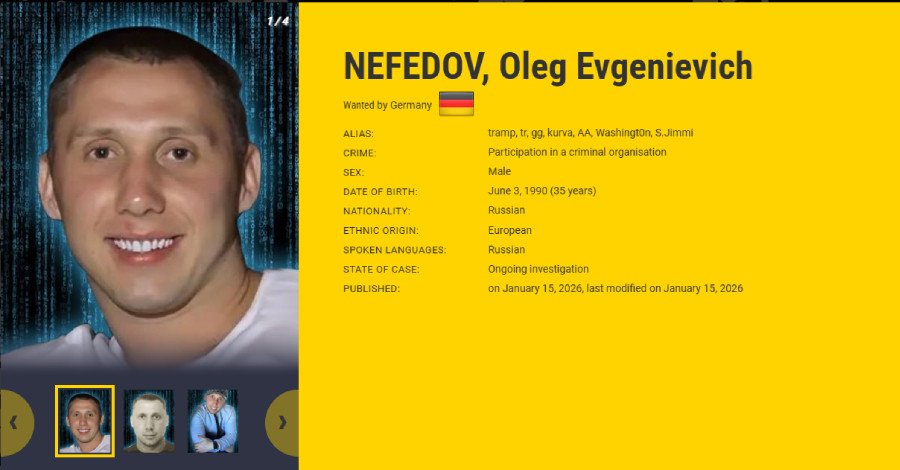
In a significant breakthrough against global cybercrime, law enforcement agencies have unmasked and are actively pursuing the alleged mastermind behind the notorious Black Basta ransomware-as-a-service (RaaS) group. Oleg Evgenievich Nefedov, a 35-year-old Russian national, has been added to both the European Union’s Most Wanted and INTERPOL’s Red Notice lists, marking a critical escalation in the fight against digital extortion.
Unmasking the Black Basta Mastermind
The joint efforts of Ukrainian and German law enforcement have led to the identification of Nefedov as the ringleader of Black Basta, a group responsible for crippling cyberattacks on over 500 companies across North America, Europe, and Australia since its emergence in April 2022. The group is estimated to have amassed hundreds of millions of dollars in cryptocurrency from its illicit activities.
The investigation also led to the identification of two Ukrainian individuals suspected of providing technical support to the Russia-linked syndicate. These suspects, described by the Cyber Police of Ukraine as “hash crackers,” specialized in breaching protected systems by extracting passwords using sophisticated software. Once credentials were compromised, Black Basta members would infiltrate corporate networks, deploy their ransomware, and demand hefty payments for data recovery.
Authorities have already conducted raids at the residences of the accused in Ivano-Frankivsk and Lviv, seizing digital storage devices and cryptocurrency assets, further cementing the evidence against the network.
The Modus Operandi: How Black Basta Operated
Germany’s Federal Criminal Police Office (BKA) provided a stark outline of Nefedov’s central role. “He served as the head of the group. As such, he decided who or which organisations would be the targets of attacks, recruited members, assigned them tasks, took part in ransom negotiations, managed the ransom obtained by extortion, and used it to pay the members of the group,” the BKA stated. This paints a clear picture of a highly organized criminal enterprise with Nefedov at its helm, orchestrating every facet of its destructive operations.
A Web of Deception: Aliases and Alleged State Ties
The unmasking of Nefedov largely stems from a trove of Black Basta’s internal chat logs leaked online last year. These logs offered an unprecedented look into the group’s structure, key members, and the vulnerabilities they exploited. Crucially, the dossier identified Nefedov as the leader, revealing his use of multiple aliases, including Tramp, Trump, GG, and AA.
Even more disturbingly, some documents within the leaked data alleged Nefedov’s connections to high-ranking Russian politicians and intelligence agencies, such as the FSB and GRU. It is believed that Nefedov leveraged these powerful ties to shield his operations and evade international justice. This claim gained further traction when a Trellix analysis revealed that Nefedov managed to secure his freedom despite an arrest in Yerevan, Armenia, in June 2024. His other known aliases include kurva, Washingt0n, and S.Jimmi. While he is believed to be in Russia, his precise whereabouts remain unknown.
The Conti Connection and Ransomware’s Evolving Threat
Evidence also links Nefedov to Conti, a formidable, now-defunct ransomware group that emerged in 2020 as a successor to Ryuk. The U.S. State Department had previously offered a $10 million reward for information on five individuals associated with Conti, including one known as “Tramp” – an alias also used by Nefedov. Black Basta itself emerged as an autonomous entity alongside BlackByte and KaraKurt following the retirement of the Conti brand in 2022, suggesting a direct lineage and shared expertise among these criminal syndicates.
The Apparent Demise and Inevitable Rebirth
The leaks and subsequent law enforcement pressure appear to have dealt a significant blow to Black Basta. The group has remained silent since February, and its data leak site was taken down later that month, signaling an apparent demise. However, the cybersecurity landscape is rife with examples of ransomware gangs that “shut down,” only to rebrand and reemerge under new identities, often with the same core members and tactics.
From Black Basta to CACTUS: A Familiar Pattern
Indeed, reports from cybersecurity firms ReliaQuest and Trend Micro suggest that several former Black Basta affiliates may have already migrated to the CACTUS ransomware operation. This assessment is based on a notable surge in organizations listed on CACTUS’s data leak site in February 2025, a timeframe that directly coincides with Black Basta’s site going offline. This pattern underscores the persistent challenge faced by law enforcement: dismantling one group often leads to the rapid formation or reinforcement of another, perpetuating the cycle of cyber extortion.
The global hunt for Oleg Evgenievich Nefedov serves as a stark reminder of the sophisticated and interconnected nature of modern cybercrime, and the relentless efforts required to bring its perpetrators to justice.
For more details, visit our website.
Source: Link