CodeBreach: How a Subtle AWS Misconfiguration Nearly Unleashed a Supply Chain Nightmare
A critical misconfiguration within Amazon Web Services (AWS) CodeBuild recently came to light, revealing a vulnerability that could have granted attackers complete control over some of AWS’s own GitHub repositories. Dubbed ‘CodeBreach’ by cloud security firm Wiz, this flaw presented a pathway for potential supply chain attacks, threatening the integrity of the AWS JavaScript SDK and, by extension, countless AWS environments globally.
The issue was responsibly disclosed to AWS on August 25, 2025, and swiftly remediated by September 2025. According to Wiz researchers Yuval Avrahami and Nir Ohfeld, exploiting CodeBreach could have led to a "platform-wide compromise, potentially affecting not just the countless applications depending on the SDK, but the Console itself, threatening every AWS account."
The CodeBreach Vulnerability Unpacked
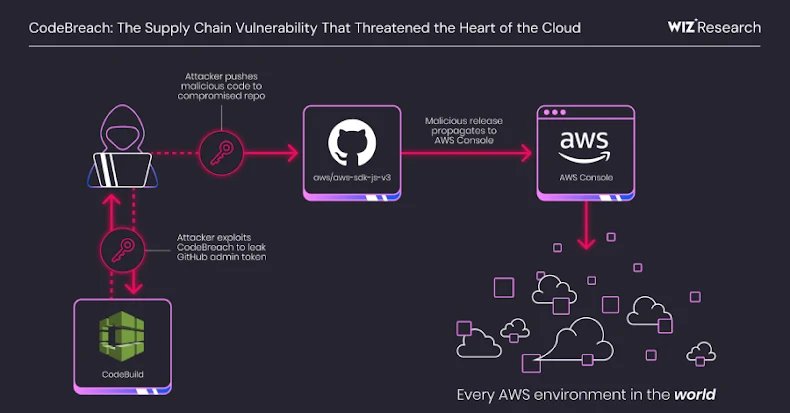
At its core, CodeBreach stemmed from a weakness in the continuous integration (CI) pipelines. This vulnerability could have allowed unauthenticated attackers to breach the build environment, pilfer privileged credentials such as GitHub admin tokens, and then leverage these tokens to push malicious code to compromised repositories. Such an action would lay the groundwork for devastating supply chain attacks, injecting malicious code into widely used software components.
The problem specifically undermined webhook filters, a security mechanism designed by AWS to ensure that only trusted events trigger a CI build. These filters are crucial for preventing untrusted pull requests from initiating potentially harmful build processes. For instance, AWS CodeBuild can be configured to trigger a build only when code changes are committed to a specific branch or when a GitHub account ID (ACTOR_ID) matches a predefined regular expression pattern.
A Flaw in the Filters: The ACTOR_ID Bypass
The misconfiguration impacted several AWS-managed open-source GitHub repositories configured to run builds on pull requests, including aws-sdk-js-v3, aws-lc, amazon-corretto-crypto-provider, and awslabs/open-data-registry. These four projects, all utilizing an ACTOR_ID filter, suffered from a "fatal flaw":
- They failed to include the essential start (
^) and end ($) anchors in their regular expression (regex) patterns.
Without these anchors, the regex pattern allowed any GitHub user ID that was a superstring of an approved ID (e.g., 755743) to bypass the filter and trigger a build. Given that GitHub assigns numeric user IDs sequentially, Wiz researchers ingeniously predicted that new 9-digit user IDs would "eclipse" a trusted 6-digit maintainer’s ID approximately every five days. By combining this insight with the automated creation of GitHub Apps (which generate corresponding bot users), they could generate a target ID (e.g., 226755743) through hundreds of new bot user registrations.
Escalation to Full Control
Once armed with a valid actor ID, an attacker could trigger a build and obtain the GitHub credentials associated with the aws-sdk-js-v3 CodeBuild project. Specifically, this would yield a Personal Access Token (PAT) belonging to the aws-sdk-js-automation user, which held full administrative privileges over the repository. With this elevated access, an attacker could:
- Push code directly to the main branch.
- Approve pull requests.
- Exfiltrate repository secrets.
These actions would effectively set the stage for a wide-ranging supply chain attack, compromising any system or application dependent on the affected SDK.
AWS’s Swift Response and Remediation
In an advisory, AWS confirmed the vulnerability, stating, "The above repositories’ configured regular expressions for AWS CodeBuild webhook filters intended to limit trusted actor IDs were insufficient, allowing a predictably acquired actor ID to gain administrative permissions for the affected repositories." AWS clarified that these were "project-specific misconfigurations in webhook actor ID filters for these repositories and not an issue in the CodeBuild service itself."
Amazon promptly remediated the identified issues and implemented additional mitigations, including credential rotations and enhanced security measures for build processes handling GitHub tokens or other in-memory credentials. Crucially, AWS found no evidence of CodeBreach being exploited in the wild.
Fortifying Your CI/CD Pipelines: Key Mitigations
To prevent similar risks, organizations leveraging AWS CodeBuild and GitHub should adhere to several best practices:
- Enable Pull Request Comment Approval: Prevent untrusted contributions from automatically triggering privileged CI/CD pipelines.
- Use CodeBuild-Hosted Runners: Manage build triggers securely via GitHub workflows.
- Anchor Regex Patterns: Ensure all regex patterns in webhook filters include start (
^) and end ($) anchors for exact matches. - Unique and Limited PATs: Generate a unique Personal Access Token for each CodeBuild project and restrict its permissions to the absolute minimum required.
- Dedicated Unprivileged Accounts: Consider using a dedicated, unprivileged GitHub account specifically for CodeBuild integration.
The Broader Lesson: CI/CD as a Prime Target
"This vulnerability is a textbook example of why adversaries target CI/CD environments: a subtle, easily overlooked flaw that can be exploited for massive impact," noted Wiz researchers. They emphasized that the "combination of complexity, untrusted data, and privileged credentials creates a perfect storm for high-impact breaches that require no prior access."
This incident underscores a recurring theme in cybersecurity. CI/CD pipeline security has come under increasing scrutiny, with past research, such as that from Sysdig, detailing how insecure GitHub Actions workflows could be exploited to leak privileged tokens and gain unauthorized access. The CodeBreach vulnerability serves as a stark reminder that even seemingly minor misconfigurations in complex cloud and DevOps environments can have far-reaching and severe consequences.
For more details, visit our website.
Source: Link