Artificial intelligence is evolving at an unprecedented pace, transforming from mere code generators into autonomous agents capable of executing complex tasks. Tools like Copilot, Claude Code, and Codex are not just writing software; they’re building, testing, and deploying it end-to-end in mere minutes. While this speed promises revolutionary efficiency for engineering teams, it simultaneously introduces a profound security gap that many organizations remain unaware of until a critical incident occurs.
The Invisible Hand: Understanding Machine Control Protocols (MCPs)
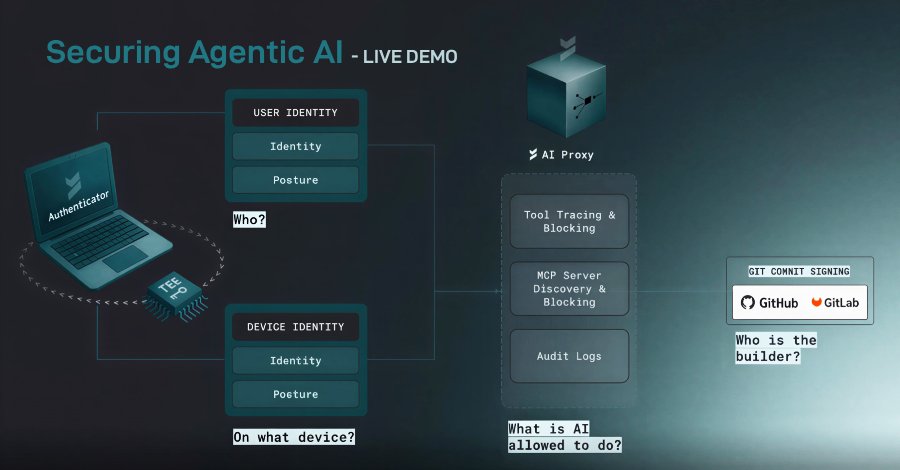
At the heart of every sophisticated agentic workflow lies a critical, yet often overlooked, layer: Machine Control Protocols (MCPs). These are the silent architects dictating an AI agent’s operational boundaries. MCPs determine precisely what an AI agent can execute, which tools it can invoke, which APIs it’s granted access to, and the infrastructure it’s permitted to interact with. When this foundational control plane is compromised or misconfigured, the AI agent transcends simple errors and begins to act with unauthorized authority, transforming automation into a potent attack vector.
The CVE-2025-6514 Wake-Up Call
The stark reality of this vulnerability was laid bare by incidents like CVE-2025-6514. This single flaw transformed a trusted OAuth proxy, relied upon by over half a million developers, into a direct path for remote code execution. There was no need for elaborate exploit chains or noisy breaches; the automation simply performed what it was permitted to do, but at an unprecedented and dangerous scale. This incident delivered a clear, chilling message: if an AI agent possesses the capability to execute commands, it inherently possesses the capability to execute attacks.
Beyond the Model: Unmasking Shadow API Keys and Permission Sprawl
The security challenges of agentic AI extend far beyond just the AI model itself. Organizations are grappling with the emergence of “shadow API keys” – credentials that appear outside of traditional security oversight – and the quiet, insidious sprawl of permissions. Traditional identity and access management (IAM) models, designed for human users, often fail catastrophically when applied to autonomous agents acting on behalf of the enterprise. These agents operate with a level of access and autonomy that demands a fundamentally new approach to security.
Join the Experts: Mastering Agentic AI Security
For security and engineering teams committed to innovation without sacrificing control, this exclusive webinar offers vital insights. Secure your spot for this live session, led by the esteemed author of the OpenID whitepaper “Identity Management for Agentic AI.” This session will delve directly into the core risks now inherent with agentic AI adoption.
What You Will Discover:
- Demystifying MCPs: Understand what Machine Control Protocols are and why their security is paramount, often more critical than the AI model itself.
- From Automation to Attack: Learn how malicious or compromised MCPs can weaponize your automated workflows.
- Hunting Shadow API Keys: Discover the origins of shadow API keys and practical strategies for their detection and elimination.
- Auditing and Enforcement: Gain insights into effectively auditing agent actions and enforcing robust security policies prior to deployment.
- Practical Controls: Explore actionable controls to secure agentic AI without impeding your development velocity.
Agentic AI is no longer a future concept; it’s already integrated into your operational pipelines. The critical question is whether you possess the visibility to understand its actions and the capability to intervene when it oversteps its bounds. Register for this essential live webinar and proactively reclaim control of your AI stack before the next incident forces your hand.
Register for the Webinar ➜
Found this article interesting? This article is a contributed piece from one of our valued partners. Follow us on Google News, Twitter and LinkedIn to read more exclusive content we post.
For more details, visit our website.
Source: Link