A New Frontier in Supply Chain Attacks: n8n’s OAuth Tokens Targeted
The digital landscape is abuzz with news of a sophisticated supply chain attack that has explicitly targeted the n8n workflow automation platform. Threat actors have been observed deploying a series of eight malicious packages on the npm registry, cunningly disguised as legitimate integrations for n8n. Their ultimate goal? To pilfer developers’ sensitive OAuth credentials, marking a significant escalation in the ongoing battle against software supply chain threats.
Unlike conventional npm malware, which typically aims for developer credentials, this campaign has set its sights on workflow automation platforms like n8n. These platforms, as highlighted by Endor Labs in a recent report, function as centralized credential vaults, housing a treasure trove of OAuth tokens, API keys, and other critical credentials for numerous integrated services such as Google Ads, Stripe, and Salesforce.
The Deceptive Tactics: How Attackers Infiltrated n8n Ecosystems
Masquerading as Essential Integrations
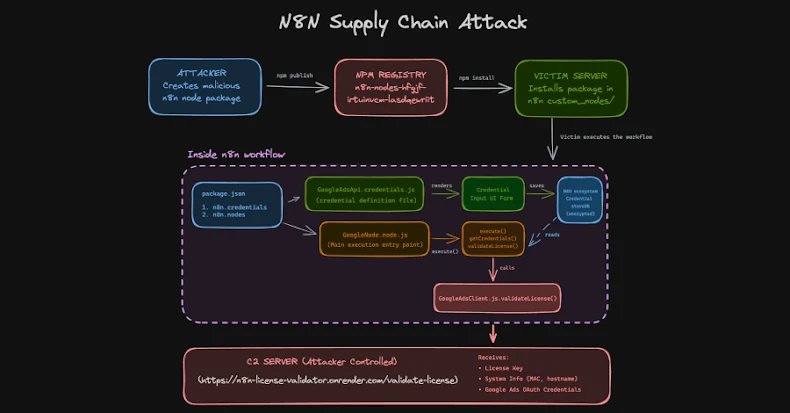
The attackers’ strategy was insidious yet effective. One prominent example, a package named “n8n-nodes-hfgjf-irtuinvcm-lasdqewriit,” mimicked a Google Ads integration. Users were prompted to link their advertising accounts through what appeared to be a legitimate form, only for their credentials to be siphoned off to servers controlled by the attackers. This exploitation of trust in community-contributed integrations allowed bad actors to achieve their nefarious goals.
Identified Threats and Lingering Risks
A list of the identified malicious packages, which have since been removed, includes:
- n8n-nodes-hfgjf-irtuinvcm-lasdqewriit (4,241 downloads, author: kakashi-hatake)
- n8n-nodes-ggdv-hdfvcnnje-uyrokvbkl (1,657 downloads, author: kakashi-hatake)
- n8n-nodes-vbmkajdsa-uehfitvv-ueqjhhhksdlkkmz (1,493 downloads, author: kakashi-hatake)
n8n-nodes-performance-metrics (752 downloads, author: hezi109)
- n8n-nodes-gasdhgfuy-rejerw-ytjsadx (8,385 downloads, author: zabuza-momochi)
- n8n-nodes-danev (5,525 downloads, author: dan_even_segler)
- n8n-nodes-rooyai-model (1,731 downloads, author: haggags)
- n8n-nodes-zalo-vietts (4,241 downloads, authors: vietts_code and diendh)
Worryingly, several authors linked to these packages—”zabuza-momochi,” “dan_even_segler,” and “diendh”—are also associated with other libraries still available for download. While an initial assessment of some of these libraries (e.g., n8n-nodes-gg-udhasudsh-hgjkhg-official, n8n-nodes-danev-test-project, @diendh/n8n-nodes-tiktok-v2) by ReversingLabs Spectra Assure found no immediate security issues, the package “n8n-nodes-zl-vietts” was flagged for containing components with a malware history. The recent update to “n8n-nodes-gg-udhasudsh-hgjkhg-official” further suggests that this campaign may still be active.
The Technical Breakdown: How Tokens Are Exfiltrated
Once installed as a community node, the malicious package operates seamlessly, mimicking a legitimate n8n integration. It displays configuration screens and saves the Google Ads account OAuth tokens, initially in an encrypted format, to n8n’s credential store. However, when the associated workflow is executed, the malicious code springs into action. It decrypts the stored tokens using n8n’s master key and then stealthily exfiltrates them to a remote server under the attacker’s control.
Researchers Kiran Raj and Henrik Plate emphasized the critical vulnerability: “Community nodes run with the same level of access as n8n itself. They can read environment variables, access the file system, make outbound network requests, and, most critically, receive decrypted API keys and OAuth tokens during workflow execution.” They further clarified, “There is no sandboxing or isolation between node code and the n8n runtime.” This lack of isolation means a single malicious npm package can gain deep visibility into workflows, steal credentials, and communicate externally without immediate suspicion, making the npm supply chain an alarmingly effective entry point for attackers.
Protecting Your n8n Instances: Urgent Recommendations
This incident underscores the inherent security risks associated with integrating untrusted workflows, which significantly expand the attack surface. To mitigate these threats, developers and n8n users must adopt a proactive security posture:
- Thorough Auditing: Always audit packages meticulously before installation.
- Metadata Scrutiny: Carefully examine package metadata for any anomalies or suspicious details.
- Prioritize Official Integrations: Whenever possible, opt for and utilize official n8n integrations.
N8n itself has issued warnings regarding the security risks posed by community nodes from npm, highlighting their potential to execute malicious actions on the machine hosting the service. For those running self-hosted n8n instances, it is strongly advised to disable community nodes by setting the environment variable N8N_COMMUNITY_PACKAGES_ENABLED to false.
Vigilance and adherence to best security practices are paramount in safeguarding your workflow automation environments against these evolving supply chain threats.
For more details, visit our website.
Source: Link