Unmasking the Digital Architects: Service Providers Fueling Industrial-Scale ‘Pig Butchering’ Fraud
In a chilling exposé, cybersecurity researchers have pulled back the curtain on the shadowy infrastructure powering the global phenomenon of “pig butchering” fraud. This sophisticated, industrial-scale scam, notorious for its devastating financial and human cost, is being enabled by a sinister network of service providers offering everything from stolen identities to turnkey scam platforms.
The Human Cost of a Digital Deception
Often referred to as “romance baiting,” pig butchering scams lure victims into fake romantic relationships or investment opportunities, ultimately defrauding them of their life savings. The scale of this operation is staggering, with Chinese-speaking criminal syndicates establishing vast scam centers across Southeast Asia. These “special economic zones” are, in reality, compounds where thousands are trafficked, their passports confiscated, and forced to perpetrate scams under threat of violence. INTERPOL has rightly characterized this as “human trafficking-fuelled fraud on an industrial scale.”
The Engine Room of Deception: PBaaS Providers
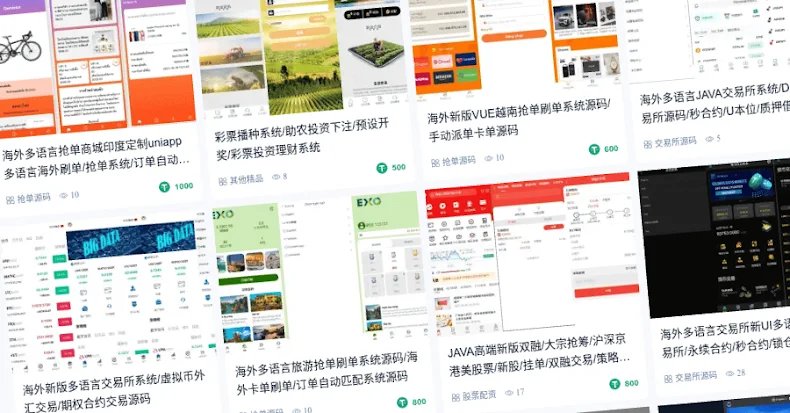
At the heart of this elaborate fraud lies a crucial ecosystem of “Pig Butchering as a Service” (PBaaS) providers. These entities supply criminal networks with the essential tools and infrastructure needed to execute social engineering operations, launder illicit funds, and move stolen cryptocurrencies beyond the reach of law enforcement. Infoblox, in a recent report, highlights how even large scam compounds like the Golden Triangle Economic Zone (GTSEZ) now rely on ready-made applications and templates from PBaaS providers.
“What once required technical expertise, or an outlay for physical infrastructure, can now be purchased as an off-the-shelf service offering everything from stolen identities and front companies to turnkey scam platforms and mobile apps, dramatically lowering the barrier to entry,” the report states.
Penguin Account Store: The Crimeware Supermarket
One prominent player in this illicit market is Penguin Account Store, also known as Heavenly Alliance or Overseas Alliance. Operating under a crimeware-as-a-service (CaaS) model, Penguin offers comprehensive “fraud kits” and scam templates. Their inventory includes “shè gōng kù” datasets – vast collections of stolen personal information belonging to Chinese citizens – alongside account data from popular social media and streaming platforms such as Twitter, Tinder, YouTube, Snapchat, Facebook, Instagram, Apple Music, OpenAI ChatGPT, Spotify, and Netflix. These credentials are believed to be sourced from information-stealing logs sold on the dark web.
Penguin’s offerings extend further, providing bulk pre-registered SIM cards, stolen social media accounts (starting from a mere $0.10), 4G/5G routers, IMSI catchers, and “character sets” – packages of stolen pictures used to create convincing fake profiles. To streamline victim engagement, Penguin has even developed a Social Customer Relationship Management (SCRM) platform called SCRM AI, designed to automate interactions on social media.
Crucially, Penguin also advertises BCD Pay, a payment processing platform directly linked to Bochuang Guarantee (博创担保自). This anonymous peer-to-peer (P2P) solution, reminiscent of HuiOne, has deep ties to the illegal online gambling space, facilitating the swift laundering of ill-gotten gains.
The CRM Backbone: Orchestrating Deception
Another vital component of the PBaaS economy is the proliferation of sophisticated Customer Relationship Management (CRM) platforms. These systems provide centralized control, allowing scam operators to manage numerous individual agents and their interactions with victims. UWORK, for instance, specializes in content and agent management tools, offering pre-made templates for creating highly convincing, yet fraudulent, investment scam websites.
Many of these scam offerings cleverly integrate with legitimate trading platforms like MetaTrader, displaying real-time financial information to lend a false sense of credibility. To further ensnare victims, these websites often feature a Know Your Customer (KYC) panel, demanding identity verification documents. An administrator panel grants the scam operators a high-level overview of the entire operation, enabling them to create agent profiles and monitor victim interactions.
“The admin panel offers everything needed to run a pig butchering operation. Multiple email templates, user management, agent management, profitability metrics, as well as chat and email records,” Infoblox reveals. “The management of agents is very complex, and agents can even be affiliates of one another,” creating a multi-layered deception.
Beyond Websites: Mobile App Deception
PBaaS suppliers are also pushing the boundaries by developing and distributing malicious mobile applications for both Android and iOS. These apps are often distributed via APK files or by enrolling a limited number of Apple devices into testing programs to circumvent stringent app store controls. Some threat actors have even gone a step further, releasing these apps directly onto official app marketplaces, cleverly disguising their fraudulent functionality by masquerading as seemingly harmless news applications. Once installed, these apps become powerful tools for manipulating victims, often posing as legitimate trading platforms to facilitate further fraud.
A Global Threat Demanding Global Vigilance
The rise of PBaaS providers has dramatically lowered the barrier to entry for cybercriminals, transforming individual acts of fraud into an industrial-scale enterprise. This sophisticated ecosystem, fueled by human trafficking and enabled by cutting-edge digital tools, represents a significant global threat. As these services evolve, so too must our collective efforts to expose, disrupt, and ultimately dismantle the architects of this devastating deception.
For more details, visit our website.
Source: Link