Google Cloud’s Trust Exploited in Widespread Phishing Campaign
A sophisticated phishing campaign has been uncovered, revealing how cybercriminals are leveraging legitimate Google Cloud services to bypass traditional email security and deceive users. Cybersecurity researchers have detailed an alarming tactic where attackers impersonate official Google-generated messages by abusing Google Cloud’s Application Integration service to dispatch malicious emails.
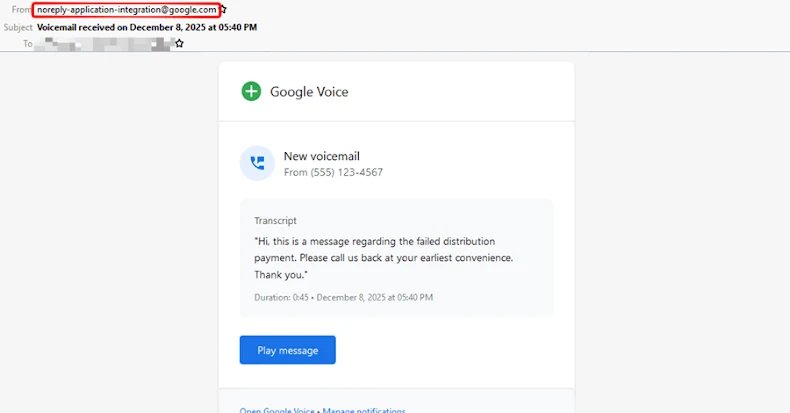
This insidious approach capitalizes on the inherent trust associated with Google Cloud infrastructure. By sending emails from a seemingly legitimate address, “noreply-application-integration@google[.]com,” threat actors successfully circumvent DMARC and SPF checks, significantly increasing their chances of landing directly in users’ inboxes. “The emails mimic routine enterprise notifications such as voicemail alerts and file access or permission requests, making them appear normal and trustworthy to recipients,” noted cybersecurity firm Check Point.
The Scale of Deception: Thousands Targeted Globally
Over a recent 14-day period observed in December, attackers unleashed 9,394 phishing emails, targeting approximately 3,200 customers across diverse geographies including the U.S., Asia-Pacific, Europe, Canada, and Latin America.
At the core of this campaign is the abuse of Application Integration’s “Send Email” task, a feature designed to allow users to send custom email notifications from an integration. While Google’s documentation specifies a maximum of 30 recipients per task, the ability to configure these emails to any arbitrary address demonstrates a clear misuse of a legitimate automation capability. The emails were meticulously crafted to mirror Google’s notification style and structure, employing familiar formatting and language to further enhance their credibility.
Common lures included fabricated voicemail messages or claims of granted access to shared files, such as a “Q4” document, all designed to prompt recipients into clicking embedded malicious links.
Multi-Stage Attack: From Trusted Links to Credential Theft
The attack chain is a carefully orchestrated multi-stage redirection flow, beginning with a click on a link hosted on storage.cloud.google[.]com – another trusted Google Cloud service. This initial step is crucial for lowering user suspicion and lending a veneer of legitimacy to the operation.
Users are then redirected to content served from googleusercontent[.]com, where they encounter a fake CAPTCHA or image-based verification. This seemingly innocuous step serves as a sophisticated barrier, designed to block automated scanners and security tools from scrutinizing the attack infrastructure, while allowing real users to proceed.
Once this validation phase is complete, victims are led to a convincing, yet fake, Microsoft login page hosted on a non-Microsoft domain. Here, any entered credentials are stolen, granting attackers unauthorized access to sensitive accounts.
Google’s Response and Targeted Industries
In response to these findings, Google has taken swift action, blocking the phishing efforts that exploit the email notification feature within Google Cloud Application Integration and implementing further measures to prevent future misuse.
Check Point’s analysis reveals that the campaign predominantly targeted the manufacturing, technology, financial, professional services, and retail sectors. However, other verticals such as media, education, healthcare, energy, government, travel, and transportation were also singled out. “These sectors commonly rely on automated notifications, shared documents, and permission-based workflows, making Google-branded alerts especially convincing,” the firm explained. “This campaign highlights how attackers can misuse legitimate cloud automation and workflow features to distribute phishing at scale without traditional spoofing.”
The Evolving Threat: OAuth and AWS S3 Integration
Further disclosures from xorlab and Ravenmail have shed more light on the evolving nature of this credential harvesting campaign. xorlab noted that these attacks are also being leveraged for OAuth consent phishing, with fake login pages even being hosted on Amazon Web Services (AWS) S3 buckets.
“The attackers trick victims into granting a malicious Azure AD application access to their cloud resources – gaining access to Azure subscriptions, VMs, storage, and databases via delegated permissions that persist through access and refresh tokens,” xorlab detailed. The strategic use of trusted infrastructure – Google, Microsoft, and AWS – at each hop makes the attack incredibly difficult to detect or block at any single point. Regardless of the entry point, victims ultimately land on a Microsoft 365 login page, underscoring the attackers’ primary objective: M365 credentials.
For more details, visit our website.
Source: Link